Late evening of January 15, 2020, Bkav Cyber Security Company released a free tool to check the NSACrypt vulnerability on Windows 10. This vulnerability was just notified by the US National Security Agency, urging Windows 10 users to immediately update the patch because of its severity. In Vietnam, it is estimated that 2,760,000 computers are at risk of being exploited by this vulnerability.
According to the latest statistics of Bkav, 60% of users checking for the vulnerability by Bkav's free tool have not updated the operating system to patch the NSACrypt.
Bkav's free tool helps users quickly check their computers for the vulnerability and also helps users update the patch. Users do not need to install, but can run immediately to scan at: https://whitehat.vn/downloadtf/BkavNSACrypt.exe.
How to use Bkav tool to check for the NSACrypt:
Step 1: Run the tool, click Check. The tool will notify if the computer is vulnerable or not and the operating system version to be updated.
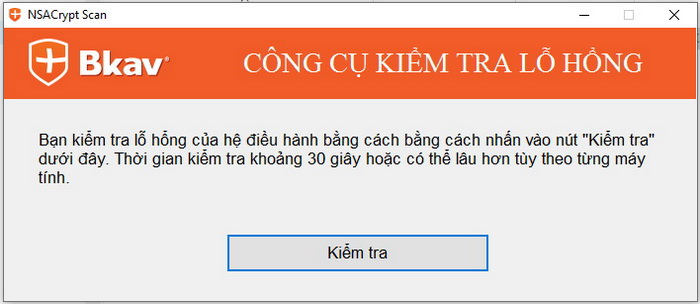
You can check the vulnerability of the operating system by click the “Check (Kiểm tra)” below. The checking time is about 30 seconds or longer depending on each computer.
Step 2: If you need to download the patch, the tool will display a notification, click OK to download. Select the corresponding patch and download.
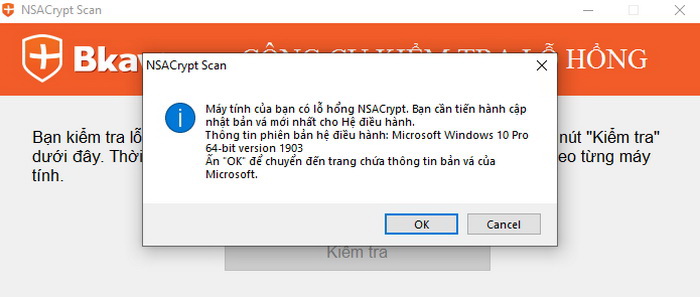
Your computer is vulnerable. You need to update the latest patch for the operating syste.
The version of operation system: Microsoft Windows 10 Pro 64-bit version 1903
Click “OK” to move to the Microsoft page of patches.
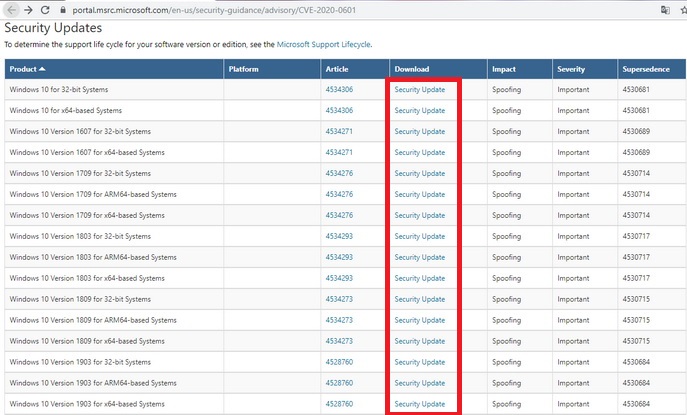
Step 3: Run the downloaded patch to fix the vulnerability
The NSACrypto vulnerability, CVE-2020-0601, resides in the way Crypt32.dll module in Windows Crypto API validates Elliptic Curve Cryptography (ECC) certificates that is currently the industry standard for public-key cryptography and used in the majority of SSL/TLS certificates.
Exploitation of the vulnerability allows attackers to abuse validation of trust between HTTPS connections, signed files and emails, and signed executable code launched as user-mode processes, then spoofing digital signatures on software, tricking the operating system into installing malicious software while impersonating the identity of any legitimate software without users' knowledge.
This is the first security flaw in Windows operating system that the NSA reported responsibly to Microsoft, unlike the Eternalblue SMB flaw, which caused the 2017 WannaCry disaster, that the agency kept secret for at least five years.
Bkav