Millions of computers have been infected with metamorphic viruses. W32.Sality.PE and W32.Vetor.PE constantly dominate the statistics table of the most infectious virus. Metamorphic virus has become a real challenge not only to users but also antivirus vendors.
Metamorphic virus is the high profile generation of the previous polymorphic viruses. Polymorphic viruses are the one which are able to automatically transform its own command code to generate different variants each time they run. Meanwhile, normal viruses keep their command codes intact after each infection, or in other words, they have only one variant. The ability to mutate enables polymorphic viruses to sophisticatedly hide themselves from the pattern recognition of antivirus softwares.
Metamorphic virus combines multiple polymorphic techniques. They use genetic algorithm to reprogram themselves, producing their F1, F2 virus generations. The longer metamorphic viruses stay in a computer, the more variants they produce and the more sophisticated the variants are, making it increasingly hard for antivirus softwares to detect and disinfect.
According to the statistics from Bkav metamorphic virus removal system, in the past year, there have been 2.2 million computers infected with this kind of virus.
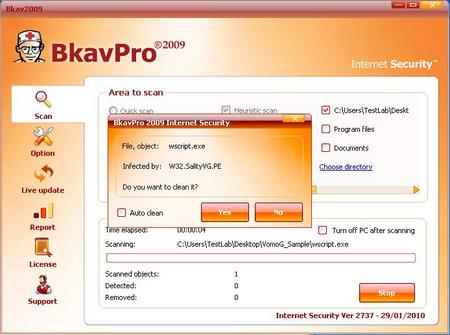
W32.Sality.PE is one of the metamorphic viruses
Metamorphic viruses are more dangerous than other kinds of viruses. They cause serious damage to the system, leading to data loss and reducing system security.
Massive fake antivirus softwares
Massive bogus antivirus softwares have been emerging in quite a short period of time, bewildering global users.
Hackers entice users to visit rouge online virus scanning websites which have identical Windows' interface by sending fake emails or taking advantage of search engines.
Then users will receive massive warnings about virus infections and are recommended to click a button to remove virus. If they follow these bogus recommendations they will download a fake AV onto their system.
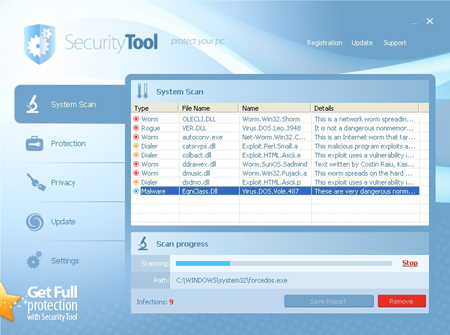
Fake AV
These fake AVs after being installed onto the system will then continue to pop up warnings about system infections, panicking users. A lot of users resort buying such softwares hoping to handle the issue, but actually they pay for the virus downloaded to their computers.
According to Bkav virus monitoring system, as many as 744 fake AVs have been emerging this year with thousands of variants namely W32.FakeAntivirERZ.Adware, W32.FakeSecuritySUI.Adware, W32.FakeAvVbs.Worm hay W32.FakeAVScanAD.Adware... At least 258,000 computers in Vietnam have been infected with these bogus softwares.
Users need to take caution on web surfing. Do not download any unknown softwares.
Emergence of new virus technics
In 2009, new virus types not only increase in number but also appear with more novel and sophisticated methods of spreading and destroying. According to a research of Bkav, there are, at least, two new technics which have not been employed by the previous virus generation.
The first to mention is W32.Induc.PE which spreads by attacking Borland Delphi compiler instead of directly infecting application softwares. This means that if a programmer's computer has been infected with W32.Induc.PE, the software written on the computer will also be infected. Thus, it's likely that malicious code has been appended to users' softwares written by Delphi.
Next is a type of Trojan which can wiretap Skype conversations. Though Skype has been using public encryption method to protect its data, a newly emerged malware is able to eavesdrop Skype users' conversations. This malware is recognized as W32.Perskyspy.Trojan by Bkav.
This Trojan intercepts the transmitting process between Audio device driver and Skype process:
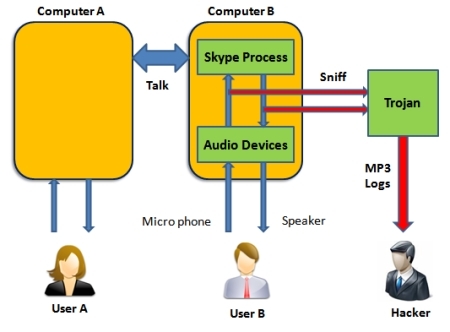
Peskyspy's wiretapping diagram
By inline hooking into functions of DirectX and Multimedia audio controller, W32.Peskyspy.Trojan will gain control over the data transmitted between Skype and Audio devices. Then, it will extract audio data, compress it into MP3 format and send it to hacker.
Predictions of virus situation in 2010
In 2010, viruses will continue to appear every day in increasingly number, especially dangerous ones such as metamorphic viruses and system files overwriting viruses. 2010 will see the proliferation of fake AV softwares targeting naive and off-guard users. Once it is getting harder in using techniques to directly attack users' computers, hackers will turn to social engineering techniques. For example, right after Microsoft released a relatively strict UAC mechanism (User Account Control), providing high level security, which grants users all the executing decisions, viruses spoofing Windows 7 notifications immediately emerged, tricking users into executing malicious code.
Mobile phones will become the new target of hackers. In 2010, phishing attacks and virus propagation targeting mobile phones will continue to increase.
Attacks against mobiles can be much more dangerous than those targeting computers and Internet since users rarely take caution with the personal devices that they always get in hand. Meanwhile, with the increasing popularity of 3G, a lot of confidential and important data such as financial data, personal information, etc. are stored, updated and transacted on mobile phone.
Bkav