On Febuary 14, Bkav Honey pot has issued a warning about a targeted attack by foreign hackers aiming at Vietnam's Public Servers. Particularly, this time hackers’ targets are servers only, while previous ransomware usually attacked workstations.
The origins of attacks are Russia, Europe and America. Servers of many agencies and organizations in Vietnam have been hacked and data on these systems have got encrypted. There are currently no statistics, but according to Bkav's estimates, by the end of afternoon 14/2 the number of victims may have reached hundreds.
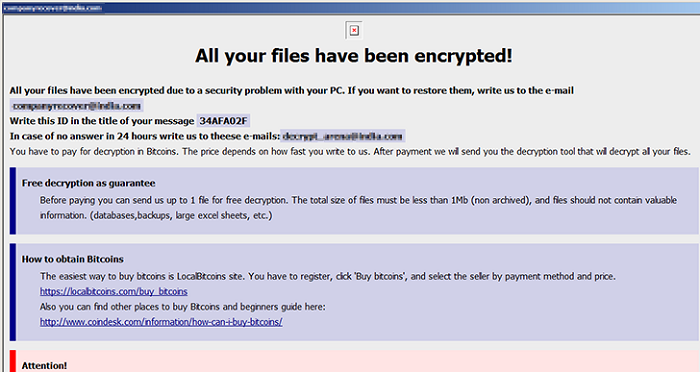
Hackers’ method is scanning for Windows servers of agencies and organizations in Vietnam, then using brute force to guess those systems’ passwords If successfully, hackers will login the systems via the remote desktop service, install ransomware on the victims’ machines.
The data encrypted includes document files, database files, executable files, etc. Victims who want to retrieve data must pay hackers. Hackers do not disclose the amount of money as usual, but require victims to contact via email for specific discussions and agreements. According to Bkav's record, with each server, hackers leave a different email to contact.
Currently, Bkav has updated the sample of W32.WeakPass into Bkav antivirus software versions, including the free version, administrators can download to scan their computers.. However, in order to prevent this type of attack, Bkav recommends that administrators need to plan to immediately check all the servers, especially the public servers, use strong password , and disable the remote desktop service if not really necessary. In case it is still necessary to maintain the service, remote access should be limited to fixed IP addresses.
Bkav