A targeted campaign using the RedHook malware is stealing personal data, banking information, and taking full control of Android devices in Vietnam. Hackers have set up fake websites impersonating government agencies and reputable financial institutions, such as the State Bank of Vietnam (SBV), Sacombank (Sacombank Pay), Central Power Corporation (EVNCPC), and the Vehicle Registration Scheduling System (TTDK). They disguise the malware as legitimate applications and trick users into downloading it via various methods—sending emails, messages through chat apps, or running advertisements on search engines.

The fake apps are named almost identically to legitimate ones, with only the file extension differing (e.g., SBV.apk). They are hosted on Amazon S3 cloud storage, allowing attackers to easily update, modify, and conceal malicious content. Once installed, the fake app requests deep system permissions, including Accessibility and Overlay rights. When combined, these permissions enable hackers to monitor user actions, read SMS content, capture OTP codes, access contacts, and even perform actions on behalf of the user without leaving visible traces.
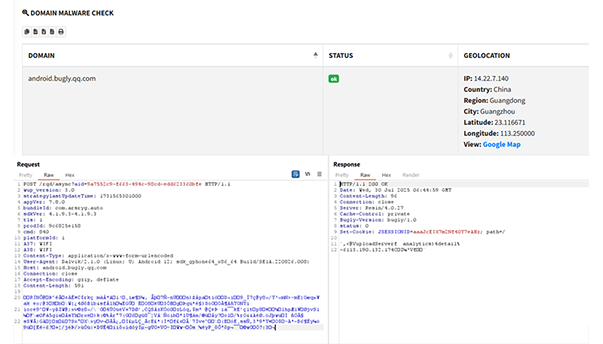
Data stolen from infected devices is compressed using gzip and sent to the malware’s C&C servers.
Reverse-engineering RedHook’s source code, Bkav’s Malware Analysis Center discovered the virus contains 34 remote control commands, including taking screenshots, sending/receiving SMS, installing or uninstalling apps, locking/unlocking the device, and executing system commands. It uses the MediaProjection API to capture all on-screen content and transmit it to the command server. RedHook also employs JSON Web Token (JWT) authentication, allowing attackers to maintain device control long-term—even after a reboot.
Analysis revealed numerous Chinese-language code strings and UI elements, along with other clear indicators of the malware’s Chinese origin. The campaign is linked to previous fraud operations in Vietnam. For example, the use of the domain mailisa[.]me—associated with a well-known beauty service exploited in past attacks—suggests that RedHook is part of a coordinated, technically sophisticated cybercrime operation. C&C domains used in the campaign include api9.iosgaxx423.xyz and skt9.iosgaxx423.xyz, both anonymized and hosted overseas, making them difficult to trace.
Smartphones now store large amounts of sensitive personal and financial data, making them prime targets for hackers and newly developed malware.
Bkav advises users:
-
Never install apps outside of Google Play, especially APK files received via messages, email, or social media.
-
Do not grant Accessibility permissions to unknown or unverified apps.
-
Organizations should deploy access monitoring, DNS filtering, and alerting for connections to suspicious domains linked to malware C&C infrastructure.
-
If infection is suspected: disconnect from the Internet immediately, back up important data, perform a factory reset, change all account passwords, and contact your bank to check account status.

Bkav