Vietnam, November 27, 2017 – Bkav's security experts (from Vietnam) have successfully crafted a new mask, which beats Face ID in the way that twins unlock iPhone X. With this new research, Bkav raises the severity level to all users, instead of just some special individuals in Bkav's previous recommendations.
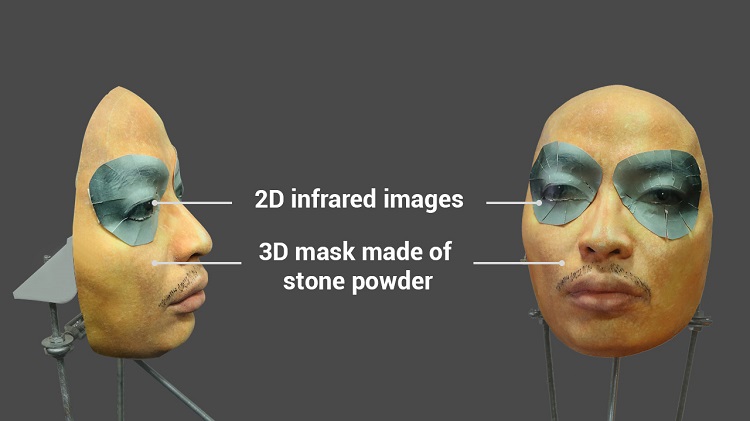
In this new experiment, Bkav used a 3D mask (which costs ~200 USD), made of stone powder, with glued 2D images of the eyes. Bkav experts found out that stone powder can replace paper tape (used in previous mask) to trick Face ID' AI at higher scores. The eyes are printed infrared images – the same technology that Face ID itself uses to detect facial image. These materials and tools are casual for anyone. An iPhone X has its highest security options enabled, then has the owner's face enrolled to set up Face ID, then is immediately put in front of the mask, iPhone X is unlocked immediately. There is absolutely no learning of Face ID with the new mask in this experiment.
Bkav names this new mask "the artificial twin", since this research has shown that the way an iPhone X unlocked by the mask is similar to by twins.
Below is the full clip of "artificial twin" mask beating Face ID:
(You can as well watch the video on YouTube here: Bkav's new mask beats Face ID in "twin way": Do not use Face ID in business transactions, or download the video here)
Mr. Ngo Tuan Anh, Bkav's Vice President of Cyber Security, said: "About 2 weeks ago, we recommended that only very important people such as national leaders, large corporation leaders, billionaires, etc. should be cautious when using Face ID. However, with this research result, we have to raise the severity level to every casual users: Face ID is not secure enough to be used in business transactions."
The vulnerability in Face ID's AI has been predicted by Bkav since Apple's iPhone X launch event, based on scientific research and analysis. As soon as iPhone X officially became available for sale, Bkav immediately conducted experiments based on previous analysis to confirm the "foreseeable" weakness. And exactly as predicted, Face ID was defeated by the mask, contrast to what Apple claimed at the iPhone X launch event. On November 15th, Bkav announced the PoC (Proof of Concept) of this experiment and said that it took around 9-10 hours to trick iPhone X's AI. Based on this principle, Bkav crafted the 2nd mask – the "artificial twin". Clearly, iPhone X is immediately tricked right after enrolling the owner's face, without 9-10 hours of work as from the previous research. This is a critical vulnerability.
In iPhone X launch event, Apple recommended: "If you happen to have an evil twin, you really need to protect your passcode where your sensitive data with a passcode". Apple's Whitepaper on Face ID also recommended: "If you're concerned about this, we recommend using a passcode to authenticate".
With this new research result, anyone can be "cloned" to make a "twin" mask of himself/herself. Thus, Bkav recommends Apple to give another recommendation similar to the twins' one, which means that iPhone X users should use passcode in all cases of sensitive data or business transactions.
Mr. Nguyen Tu Quang, CEO of Bkav Corporation, judged: "Security should approximate to absolute, and AI should only be a supplement, not the sole security base for Face ID like the way Apple is working on. AI, in any way, is now still human-made and it does at its best based on the experience of its creators and trainers, here is Apple. Thus, anyone who is more experienced than the creator can bypass it".
Bkav researchers said that making 3D model is very simple. A person can be secretly taken photos in just a few seconds when entering a room containing a pre-setup system of cameras located at different angles. Then, the photos will be processed by algorithms to make a 3D object.
It can be said that, until now, Fingerprint is still the most secure biometric technology. Collecting a fingerprint is much harder than taking photos from a distance. Meanwhile, just by taking photos from a distance to create 3D objects as mentioned above, both Apple's Face ID and Samsung's Iris Scanner can be bypassed easily.
Contact:
Ms. Sarah Do – Global Media Relations Manager
Email: ThuDT@bkav.com
Twitter: https://twitter.com/ThuDo2604
Website: http://bkav.com
--------------------------------------------------------------------------------------------------
Questions & Answers
(Updated November 27, 2017)
Q: Bkav is known as a smartphone manufacturer, so is this a kind of deframing your competitor?
Aside from being a smartphone manufacturer, Bkav is also the leading cyber security firm in Vietnam. As from 2008, Bkav was yet to develop Bphone (Bkav.com/Bphone), we were the first company in the world to show that face recognition was not an effective security measure for laptops, right after Toshiba, Lenovo, Asus, etc. used this technology for their products. In June 2017, Bkav also proved that Iris Scanner on the Samsung Galaxy S8 can be bypassed easily. Bkav is known as the security firm to discover the first critical flaw in Google Chrome just days after its launch in 2008. Bkav was also the firm to trace the master server in Britain of unprecedentedly massive DDoS attacks targeting US and Korean governments' websites in July, 2009. Thus, we had been a cyber security company prior to joining smartphone manufacturing industry. Cyber security research has always been a part of our domain.
Q: Any comments about iPhone X Face ID rejection of Korean banks?
With our new research result, we believe that it is essential. We appreciate the proper response from Korean banks.
--------------------------------------------------------------------------------------------------
The mask beats Face ID on iPhone X
(Press Release)
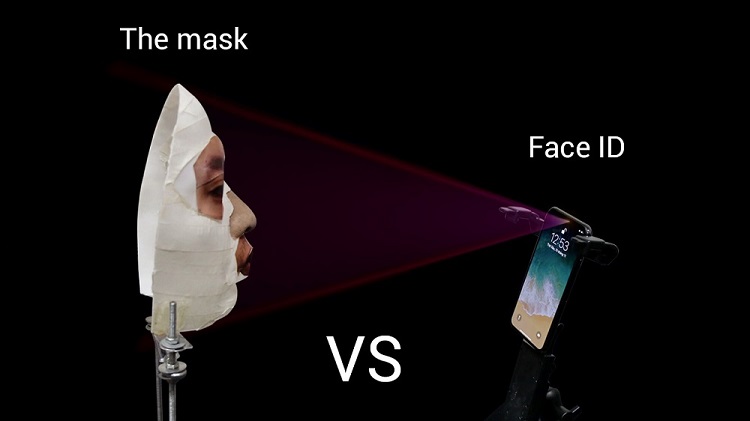
Hanoi, November 15, 2017 - Bkav Corporation today holds a demo, unveiling the principle to figure out the flaw in the iPhone X's Face ID facial recognition system, and recommends that Face ID technology is not as secure as Apple claimed.
When launching the iPhone X, Apple said it worked with professional mask makers and makeup artists in Hollywood to protect against attempts using masks to beat Face ID. Apple claimed that Face ID is more secure than Touch ID. However on November 10, a video clip by Bkav experts in Vietnam has shown that a 3D mask can easily bypass Face ID's security mechanism. This immediately got special attention from international community and media. Because many individuals and organizations all over the world have tried to bypass Face ID with thousand-dollar masks and failed. Many questions, even skepticism are posed to Bkav experts.
At the event, once again Bkav's demonstration shows that with a mask crafted through a combination of 3D printing technique, 2D images and some special processing, Bkav experts can beat Face ID on the iPhone X. Bkav experts also point out ways to break through Apple's security mechanism.
There are three key points in Face ID technology. Firstly, a photo of user is taken to create the surface of the face. Secondly, another picture is taken in form of a mesh to reproduce the face's 3D image. Both of these pictures are taken by infrared camera. The third is Face ID's ability based on AI technology to distinguish the real face and the fake one. Bkav engineers find that with 2D and 3D pictures, it is easy to create a deceptive object. AI technology might be a more complicated part. However, the vulnerability in Face ID's AI has been predicted by Bkav since the Apple's launch event, based on scientific research and analysis. As soon as the iPhone X officially went on sale, Bkav immediately conducted experiments based on previous analysis to confirm the "foreseeable" weakness.
Mr. Ngo Tuan Anh, Bkav's Vice President of Cyber Security, said: "Achilles' heel here is Apple let AI at the same time learn a lot of real faces and masks made by Hollywood's and artists. In that way, Apple's AI can only distinguish either a 100% real face or a 100% fake one. So if you create a ‘half-real half-fake' face, it can fool Apple's AI".
Mr. Ngo Tuan Anh, Bkav's Vice President of Cyber Security
With this philosophy, Bkav's experiment has confirmed that: Face ID was fooled by a mask. Also, the mask created by Bkav looks very different from other attempts' masks. "Our mask that fooled Face ID is simple but very philosophically complex to create, it requires professionals and insights on security as well as AI technology", added Mr. Ngo Tuan Anh.
Bkav's CEO, Mr. Nguyen Tu Quang also said: "AI by any way is still man-made, and it only does the best upon the experience of its creator, here is Apple. If you have more experience, then you can bypass it".
Researchers from Bkav also point out Apple's Face ID technology in particular and face recognition technology in general is not mature enough after nearly 10 years of development. At the iPhone X event, Apple claimed that Face ID can distinguish a mask from real face. Face ID technology will allow just one face to be registered per device. However, in fact, by Bkav experiment, Face ID on the iPhone X was fooled to unlock by a mask, tricked into thinking the mask to be a real face even when its two eyes were covered with 2D images, and got unlocked by both the mask and the human face. If Apple does not make any adjustments, Face ID on iPhone X is probably worse than Samsung's Iris Scanner because at least this technology, although it is also fooled by masks, is still able to distinguish the twins. Face ID is not.
Bkav's CEO, Mr. Nguyen Tu Quang
The head of Bkav, CEO Nguyen Tu Quang also confirms that Bkav's research was a PoC (Proof of Concept) - a study of the principle, not an exploit scenario. Based on this PoC, there will be exploit scenarios and fixes. Researchers have already some such scenarios but will only share with the manufacturer so as not to affect the users. "Up till now, fingerprint is still the best biometric security technology", Mr. Quang concluded.
With Face ID defeated by the mask, Bkav experts recommend that national security organizations, national leaders, large corporation leaders, billionaires, etc. should be cautious. The exploitation can be difficult for ordinary users, but simple for professionals.
For the question when making the mask, whether the researchers let the iPhone X learn the mask. Experts state they have applied the "no passcode" principle during the study, and also point out that the iPhone X in the test will not unlock when put in a different position or angle. If the iPhone X has learned the mask, it can still unlock comfortably as used by everyone when moved to another location.
For the question, the iPhone X has the protection mechanism of requiring a passcode after 5 unsuccessful match attempts, how can researchers use such finite attempts to make the mask? Bkav recited the research is to point out a PoC, which can be optimized for successful illegal unlocks up to 100%. Such limited attempts are used if only it is an exploit scenario. The company also cited its Iris Scanner bypass for example. Bkav spent 2 months before succeeded at their very first try.
Below is the full press conference held by Bkav this morning:
--------------------------------------------------------------------------------------------------
Questions & Answers
(Updated November 14, 2017)
Q: When will Bkav clarify all the doubts about the experiment?
A: A press conference is going to be held on 15/11/2017, from 9 a.m. to 10 a.m. (UTC+7). The event will be livestreamed in English here Bkav.com/ls.fid.
Q: How Face ID was set up?
A: It learns from human face, just like normal.
Q: Were you able to use the mask to unlock the iPhone immediately after freshly enrolling the real face? The reason I ask is that, according to Apple's whitepaper, Face ID will take additional captures over time and augment its enrolled Face ID data with the newly calculated mathematical representation. Can you describe precisely how you went about conducting this experiment?
A: It does not matter whether Apple Face ID "learns" new images of the face, since it will not affect the truth that Apple Face ID is not an effective security measure. However, we knew about this "learning", thus, to give a more persuasive result, we applied the strict rule of "absolutely no passcode" when crafting the mask.
Q: Can you explain why your hack worked but similar attempts (like Wired magazine's) failed?
A: Because... we are the leading cyber security firm ;) It is quite hard to make the "correct" mask without certain knowledge of security. We were able to trick Apple's AI, as mentioned in the writing, because we understood how their AI worked and how to bypass it. As in 2008, we were the first to show that face recognition was not an effective security measure for laptops (related links can be found at the end of this writing).
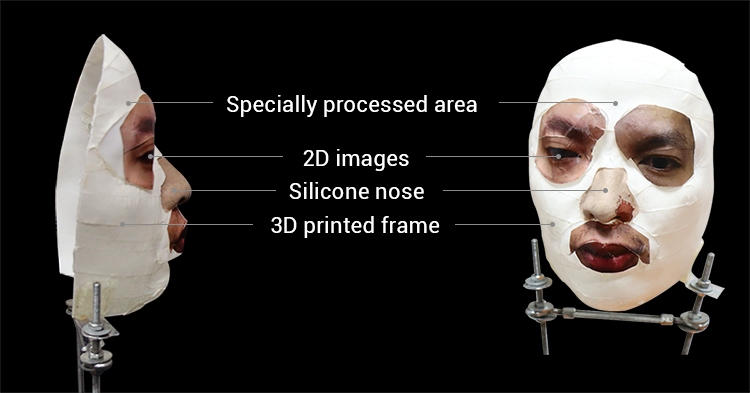
Q: How did Bkav develop the mask (for example why you use silicone for the nose, why 3D printing for some areas while special processing for others, etc.)?
A: You are right. Many people in the world have tried different kinds of masks but all failed. It is because we understand how AI of Face ID works and how to bypass it. As stated above, we were the first in the world to show that face recognition was not an effective security measure for laptops.
Q: Is 3D creation and printing difficult?
A: Not at all. It is quite simple, will be even more simple in the future. We might use smartphones with 3D scanning capabilities (like Sony XZ1); or set up a room with a 3D scanner, a few seconds is enough for the scanning (here's an example of a 3D scanning booth).
An easier way is photograph-based, artists craft a thing from its photos. Take the nose of our mask for example, its creation is not complicated at all. We had an artist make it by silicone first. Then, when we found that the nose did not perfectly meet our demand, we fixed it on our own, then the hack worked. That's why there's a part on the nose's left side that is of a different color (photo attached). So, it's easy to make the mask and beat Face ID. Here, I want to repeat that our experiment is a kind of Proof of Concept, the purpose of which is to prove a principle, other issues will be researched later.
Q: Are the dimensions of a person's face needed? How would those be obtained without a target sitting for them?
A: The 1st point is, everything went much more easily than you expect. You can try it out with your own iPhone X, the phone shall recognize you even when you cover a half of your face. It means the recognition mechanism is not as strict as you think, Apple seems to rely too much on Face ID's AI. We just need a half face to create the mask. It was even simpler than we ourselves had thought.
Apple has done this not so well. I remember reading an article on Mashable, in which Apple told that iPhone X had been planned to be rolled out in 2018, but the company then decided to release it one year earlier. This shows that they haven't carried out scientific and serious estimation before deciding to replace Touch ID with Face ID.
The 2nd point is, in cyber security, we call it Proof of Concept, which is useful for both sides, the hackers and the users. The hackers, they can find out a simpler way to exploit users' device based on such PoC. While with users, if they know about such possibility, they will not use the feature to keep themselves safe. Just like the KRACK attack, it is not easy to be successfully exploited but users are urged to update the patch ASAP, because the threats are real. With Face ID's being beaten by our mask, FBI, CIA, country leaders, leaders of major corporations, ect. are the ones that need to know about the issue, because their devices are worth illegal unlock attempts. Exploitation is difficult for normal users, but simple for professional ones.
Q: What technologies and techniques were employed to make the 3D model associated with the 3D-printed portions of the mask?
A: We used a popular 3D printer. Nose was made by a handmade artist. We use 2D printing for other parts (similar to how we tricked Face Recognition 9 years ago). The skin was also hand-made to trick Apple's AI.
Q: What's the approximate cost of the mask?
A: ~ 150 USD
Q: How long did it take to construct the mask, including the time to develop 3D models and other assets associated with its production?
A: We started working on it, including 3D models and other assets, right after receiving iPhone X on Nov 5.
Q: Who would be the target for this kind of attack?
A: Potential targets shall not be regular users, but billionaires, leaders of major corporations, nation leaders and agents like FBI need to understand the Face ID's issue. Security units' competitors, commercial rivals of corporations, and even nations might benefit from our PoC.
Q: The clip is not clear enough. Your clip and answers have not included all details. Can you record another clip of this experiement with more details?
A: I want to repeat that our experiment is a kind of Proof of Concept, the purpose of which is to prove a principle, other issues will be researched later.
Q: According to Bkav, up to now which security measure is the most secure?
A: As for biometric security, fingerprint is the best.
-----------------------------------------------------------------------------------
Face ID beaten by mask, not an effective security measure
Vietnam, November 10, 2017 - At iPhone X launch event, Apple's Senior Vice President Phil Schiller claimed that Face ID can distinguish human's real face from masks thanks to its artificial intelligence (AI). "They (Apple engineering teams) have even gone and worked with professional mask makers and makeup artists in Hollywood to protect against these attempts to beat Face ID. These are actual masks used by the engineering team to train the neural network to protect against them in Face ID. It's incredible!", Phil Schiller said (Apple's Keynote September 2017, from 1:27:10 to 1:27:26). However, one week after iPhone X officially went on sale, Bkav security experts from Vietnam show that Face ID can be fooled by mask, which means it is not an effective security measure.

"These are actual masks used by the engineering team to train the neural network to protect against them in Face ID" (Apple)
Below is the video that demonstrates how Face ID is beaten:
(You can as well watch the video on YouTube here: How Face ID be beaten by a mask, or download the video here)
Mr. Ngo Tuan Anh, Bkav's Vice President of Cyber Security, said: "The mask is crafted by combining 3D printing with makeup and 2D images, besides some special processing on the cheeks and around the face, where there are large skin areas, to fool AI of Face ID".
So, after nearly 10 years of development, face recognition is not mature enough to guarantee security for computers and smartphones. In 2008, Bkav was the first company in the world to show that face recognition was not an effective security measure for laptops, right after Toshiba, Lenovo, Asus, etc. used this technology for their products. You can find out more details in the links below (note: Bkis is the former name of Bkav):
1. Laptop face-recognition tech easy to hack, warns Black Hat researcher (Computerworld)
2. Face recognition bypass demonstration clip by Bkis at Black Hat Conference
3. Vietnamese security firm: Your face is easy to fake (CNET)
We will publish the research which helps us to craft the mask that beats Face ID in the next writing.
Bkav
About Bkav:
Established in 1995, Bkav Corporation (www.bkav.com) is the leading firm in network security, software, smartphone manufacturing (Bkav.com/Bphone) and smarthome. Bkav is the first company in the world to discover the vulnerability in face recognition log-on in laptops right after this technology started to be popular. Before, the technology was trusted to be highly accurate and was used in products of many technology companies around the world like Toshiba, Lenovo, Asus, and so on.
Bkav is known as the security firm to discover the first critical flaw in Google Chrome just days after its launch in 2008. Bkav was also the firm to trace the master server in Britain of unprecedentedly massive DDoS attacks targeting US and Korean governments' websites in July, 2009.
