The aim of connecting to the Internet is to share our information resources with people from different physical locations. Thus, resources are scattered, which means our systems can be hacked easily, causing data loss.
The wider network we communicate with, the more vulnerable we become. That's the rule. Any risk from the Internet may lead to danger. A small system error could be continuously exploited, and a serious one would immediately cause terrible damage. In such a world-wide network as the Internet, a terrible damage may result from any tiny flaw or system error.
The following chart shows the number of cyber attacks and unauthorized accesses reported to CERT (Computer Emergency Response Team).
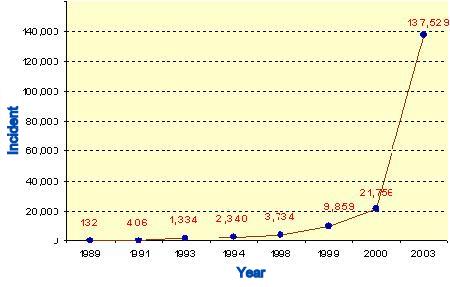
As can be seen from the chart the number of incidents, namely cyber attacks and unauthorized accesses, is increasing rapidly. Information technology is developing at an incredible rate all over the world. As "a coin always has two sides", the rapid hacking "technology" development comes as "a side of the coin", leading to the increase of data stealth, destruction and cyber attacks.
Obviously, the Internet has nowadays, become a world-wide data-swap gate, which makes individual and work communications much easier Information swapped through the Internet is increasing by exponent everyday. There are more and more enterprises, bank branches, etc.communicating with each other through the Internet.
The Internet has definitely facilitated human life and work. However, enterprises, organizations or even individuals with important data such as nation secrets, financial figures and personal information have become targets of cyber attacks. Consequences of cyber attacks range from small impacts to serious damage, such as important data deletion, personal right violation, even the overall system crash only after a few hours.
Nowhere is as insecure as the Internet. Through the Internet, if you "say a word" at this place, someone may "hear it" from thousand miles far away ("say" and "hear" insinuate the information swap among connected computers). In other words, connected people are just like those staying together in an "Internet box". They just don't see each other in flesh. Technically, every single move you make in the virtual world of 0 and 1 may be detected by the "digital eyes" (technical tools) of other millions.
If we had "digital eyes" and saw the Internet world like the one created in human brain from "Matrix" series, most of us would be shocked. In this world, "millions of people are going out with the doors unlocked, or even leaving their saving-books on open-wide windows' thresholds". Such careless people may include you and me. We don't recognize the insecurity and think that others neither. This does not mean everything will be better if we turn our backs to the Internet. The Internet has played an important role in the world development. What we need to do is to minimize the insecurity and keep our IT knowledge up-to-date, which are totally feasible. We will discuss about the know-how in the next parts.
What do we need to protect?
a. Data
With data, we should pay attention to the following factors:
-Confidentiality: Only authorized staffs have access to data
- Integrity: No modification or error allowed.
- Availability: Always available for access.
b. Resources
Computer resources can be exploited by hacker. Your computer needs protection even when there is no important information on it. Hacker may take control over your machine and use it for his attacks, which renders you evildoer.
c. Prestige
As said above, hacker can take control over computers of individuals or organizations for his cyber attacks, which damages the victim's prestige.
What attack patterns are there?
There are many attack patterns, some we have known, but some are still secrets. However, we can divide them into 4 main patterns:
1. Direct attack
Most of attacks are direct ones, in which hackers use a computer to directly attack others. These are what hackers can do:
-
Brute force search of User name and Password by trying some common words (like"hello"), user family members' names, birthdays or phone numbers, etc. Thus, do not use too simple passwords or any common ones like the above.
-
Use special tools to decode password files and work out password. Too short passwords are normally worked out by this way. Password with at least six characters are recommended.
-
Paralyze an application or an operating system exploiting their vulnerability which is like Achilles' heel. This heel can be taken advantage by hacker to attack a system.
2. Sniffing
Hacker is able to "listen to" your information swapped via the Internet. As said above, if there are tools like "digital eyes", we will see how easy sniffing is. Restrict giving out your sensitive information on the Internet.
Password sniffing: Hacker can work out your password, then gain access to your system as an authorized user. It is like finding out your home key, open the door and steal our havings.
3. Denial of Service (DoS)
A DoS attack can be caused by totally valid queries to a website's server. These requests are sent in vast number from many computers at the same time, which paralyzes website's server, renders it unable to serve any more requests for a period of time. That's Denial of Service attack.
4. Users-targeted attacks
Hacker, claiming as a certain user, may phone network administrator to ask for password change. Since the administrator does not know user by face, he is easily talked into changing account's password. Thus, if you are a network administrator, be cautious, never satisfy any demand via phone.
Using the same method, hacker may request the administrator to change the system configuration, which allows them to perform their planned attacks.
No technical prevention is effective regarding such kind of attack. Only vigilance and adequate training can afford to prevent this kind of assault.
Thus, human factor is always the weakest point in network systems.
Hackers, who are you?
There are many kinds of hackers with different purposes. However, they can be classified as follow:
5. "For fun" hackers
They are those who get bored with their daily works and want to "relax" by intruding network systems. They feel a surge of excitement in illegally intruding other users' computers. They do not aim to harm the system, but their penetrations and "foot print" eliminations may cause damage to the targeted system.
6. Destroyer
Their purpose is to destroy the system, and they enjoy doing that. These hackers cause serious damages. Fortunately, such bad guys are not common in the world.
7. High-score earner
They want to prove themselves through new kinds of attacks or the number of systems that they have intruded. Their favorite target is famous and highly secure websites.
8. Spy
Spy intrudes the system to steal data for various purposes like trading or cash.
Who are hackers? The groups depicted above are called hackers. Hackers are also virus authors or software crackers. Hackers may have good knowledge about a system. However, some of them can still afford to attack a system without knowing much about it using available tools such as cracking softwares, or viruses. In general, hackers are those who have expertise in IT, but using it for malicious purposes. Hackers must be judged. Moreover, in order to limit the increase of hackers, a stricter law system is supposed to be adopted and IT students' awareness are supposed to be fostered early.
Information Security Strategies
You have seen how insecure the Internet is, so it is very important to apply the following rules while building network systems, especially large and important ones.
a. Minimum privilege
Grant certain privilege which is required for works, and no more.
All objects namely users, applications, operating systems, etc. should obey this rule.
b. Simpleness
System should be simple enough for intelligibility and smooth operation.
Intelligibility: easy to understand the system's working principles and to get to know if it is operating as desired.
Smooth operation: the more complex the system is, the more likely error occurs during operation.
Thus, Firewall often runs on systems with unnecessary applications removed.
c. In-depth protection
Different security policies are recommended.
Multi-layer security protection is set up. If a hacker wants to attack the system, he must bypass outer layers → mutual protection.
d. Knot
All information, including information sent by hackers, must go through a knot controlled by administrator. It is like in the International port of entry where the officers check all information in and out the system.
Knot becomes useless if there is another gate.
e. Integrity
Every computer in the network even those which does not store important data or service must be protected since if a computer is compromised by a hacker, it will become means for hacker to attack other computers in the network easily.
f. Diversity
Avoid using the same operating system or software for the whole network. If all computers in your network employ Windows XP; one day, a serious flaw is found in Windows XP. Hackers can use it to illegally deleting your data, and Microsoft is yet to find a solution; you can do nothing but to turn off all computers' network and wait for Microsoft's patch. Using different operating systems and applications in a network is recommended.
h. Experts' advice
If you are not really good inset up an information security management system,you should ask for help from IT experts or specialized organizations. A small mistake in system setup and operation can lead to serious damage.
Illustrations:
How do hackers exploit software's "heel"? The following illustration gives you the answer.
SYN Defender, or Flood Attack, is one of many methods that hackers use to exploit software's flaw.
For communicating through Internet, computers use a common suite named "TCP/IP" (Transmission Control Protocol/ Internet Protocol). The suit works as a traffic light on Internet.
When two computers want to communicate or swap formation, they need to "shake hands" and "introduce themselves". The computer A wants to communicate with the computer B. Firstly, A sends a communication request ("SYN" in the following chart) to B. Computer B responses the request by sharing a part of its resources and sending an answer "SYN/ACK" to A. Then, A sends "ACK" to B to confirm its request. The communication starts right after.
1 A ----------------SYN-----------------> B
2 A <---------------SYN/ACK-------------- B
3 A ----------------ACK-----------------> B
This is how hackers do to exploit the process:
Hacker's computer is in A role, and the targeted computer is B.
A sends communication request "SYN" to B. The different thing is that, in the request, A names himself A' (faked name), a non-exist address. B responses to the request by sending "SYN/ACK" answer to A' ( instead of A). A' is a non-exist address, thus there is no "ACK" sent in return.
No "ACK" in return, but B keeps waiting for the confirmation. This is the flaw. What happens if A continues to send fake requests and B continues to response and wait? The answer is B runs out of resources and unable to serve anymore request. We call B is "flooded" by requests or got "DOS" attack. If A' is a real address, B will receive "ACK" from A' and "flood" will not happen.
1 A -----SYN-----> B
A -----SYN-----> B
A -----SYN-----> B
A -----SYN-----> B
A -----SYN-----> B
A -----SYN-----> B
2 A' <---SYN/ACK--- B
A' <---SYN/ACK--- B
...
Solutions:
There are two solutions to this prolem:
1. The first solution is "SYNDefender Relay"
-
Install Firewall as an intermediate layer. Firewall receives "SYN" from A and sends "SYN/ACK" back to A. After receiving "ACK", Firewall allows A to connect to B.
-
Only requests defined as authorized are allowed to connect to B by Firewall.
-
Firewall controls "shake hands" process, the server computer or B does not share resources and does not get flooded. The following chart gives more details:
1 A -----SYN-----> FW B
2 A <---SYN/ACK--- FW B
3 A -----ACK-----> FW -----SYN-----> B
4 A FW <---SYN/ACK--- B
5 A FW -----ACK-----> B
2. The second solution is "SYNDefender Gate"
-
Install Firewall as an intermediate layer like the first solution.
-
This solution releases "SYN/ACK" right away, even there is no "ACK" in return. The following chart will explain better:
1 A -----SYN-----> FW -----SYN-----> B
2 A FW <---SYN/ACK--- B
3 A <---SYN/ACK--- FW -----ACK-----> B
4a A -----ACK-----> FW -----ACK-----> B (or)
4b A FW ------RST----> B
10 Internet Security advices summarized as follow:
1. Encourage or require staffs to use strong password.
2. Password should be changed every 90 days.
3. Ensure that your AV program is up-to-date.
4. Remind your staffs to be serious and careful in using emails and swapping information through email.
5. Fully and comprehensively execute the Internet security solution.
6. Evaluate the Internet security situation regularly.
7. When one of your staffs no longer works for you, delete his account from your company network.
8. If your staffs work at home, provide centralized Internet security managing service.
9. Update operating system, application softwares of your company or organization regularly.
10. Disable unnecessary Internet services.
Bkav