Recently, bad guys have spread massive malware variants which have identical icons and version details as popular softwares' update programs to bypass antivirus softwares as well as system analysts. This supposedly becomes a new trend of file replacing virus.
First emerged in 2007, this type of virus has actually undergone 3 development stages:
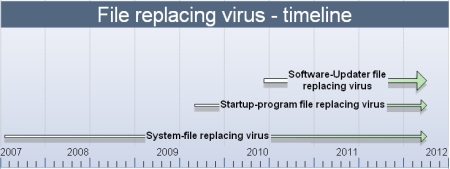
The first stage (2007) - System-file replacing virus:
The viruses aim to replace Windows system files such as: explorer.exe, userinit.exe, winlogon.exe, rpcss.dll, lpk.dll, comres.dll, etc. To keep the system operate normally, the viruses make a backup for the replaced files and refer to these files only when they have been executed. If an AV tries to remove the infection by deleting infected files without restoring replaced files, the whole computer system will be broken. Unfortunately, almost all AVs have this problem. Bkav already gave a warning on this issue at APCERT AGM.
The second stage (2009) - Startup-program file replacing virus
Instead of replacing system files, bad guys aim their arrows at startup programs. These programs are often registered under 2 following keys:
HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun
HKCUSOFTWAREMicrosoftWindowsCurrentVersionRun
The viruses still make a backup for replaced files (similar to first stage). And yet, some AV programs still make the same mistake when deleting infected files without restoring critical files.
The third stage (2010) - Software-Updater file replacing virus
Recently, there is a rising number of newly emerged viruses that overwrite software updaters. Many would mistakenly recognize them as the second stage ones. File replacing viruses in this period disguise themselves much better by faking icons, version information, etc. and overwrite updaters of some popular softwares (Adobe, DeepFreeze, Java, etc.).
Different from the two previous stages, they do not make any backup for replaced files. They only attack the software updaters, and thus do not affect the software operations. In addition, with icons and version information faked by the viruses, it is difficult to define whether the systems have been infected or not by using such tools as Autoruns, Process Explorer, etc. Obviously, this is the new strategy that is causing many difficulties to experts.
These are 3 stages of file replacing virus development. They are still changing the infection methods as bad guys never stop finding ways to introduce troubles to AVs. This requires AV vendors to continually improve their softwares rather than just "detect and delete" infected files like the way they are doing now.
For more information you can visit the following websites:
http://blog.bkis.com/en/malware-faking-adobe-update
http://blog.bkis.com/en/malware-overwrites-software-updaters-?-new-trend/
http://www.pcworld.com/businesscenter/article/192422
/new_malware_overwrites_software_updaters.html
http://www.computerworld.com/s/article/9174126
/New_malware_overwrites_software_updaters
http://news.softpedia.com/news/Trojan-Masquerades-as-Adobe-Reader
-Updater-Component-138453.shtml
http://www.theregister.co.uk/2010/03/29/software_update_trojan/
Bkav